Communication and Certificates
This topic describes how components of the Cybereason On-Prem offering communicate, as well as the certificates used to establish communication between Cybereason servers.
In this topic:
Communication ports and protocols
Source |
Destination |
Port |
Protocol |
Type |
Notes |
|---|---|---|---|---|---|
WebApp server |
Detection server |
8443 |
HTTPS |
REST |
The port number is defined by the probe_port field in the Server_Configuration.csv file. |
WebApp server |
Detection server |
7075 |
HTTPS |
REST |
This connection is used to poll malware alert data. |
WebApp server |
Registration server |
8443/443 |
HTTPS |
REST |
The port number is defined by the probe_port field in the Server_Configuration.csv file. |
Detection server |
WebApp server |
443/8443 |
HTTPS |
REST |
The port number is defined by the web_port field in the Server_Configuration.csv file. |
Registration server |
Detection server |
443/8443 |
HTTPS |
REST |
The port number is defined by the web_port field in the Server_Configuration.csv file. |
Client PC |
Configuration management server |
22 |
SSH |
N/A |
This connection uses the SSH protocol. The client PC is the PC used to install and deploy the environment, before any sensors are connected. |
Configuration management server |
All servers |
22 |
SSH |
N/A |
This connection uses the SSH protocol. The Configuration management server allows SSH and SCP connections to all Cybereason servers (Detection, Registration, Microservices and Webapp). |
Client PC |
WebApp server |
443/8443 |
HTTPS |
REST |
The port number is defined by the web_port field in the Server_Configuration.csv file. The client PC is the PC used to install and deploy the environment, before any sensors are connected. |
Client PC |
Configuration management server |
443 |
HTTPS |
N/A |
This port is used for the connection to the Ansible UI. |
MS Server (Scribe, Arbiter, Management, Ops, BWL microservices) |
MS Server (PostgreSQL) |
5432 |
TCP |
JDBC |
This is the default port as defined in the server configuration. This is an Internal Connection in the MS Server. |
Detection server, WebApp server |
MS Server (Scribe microservice) |
8081 |
HTTP/2 |
gRPC (protobuf) |
This is the default port as defined in the server configuration. |
Detection server, WebApp server |
MS Server (RabbitMQ) |
5672 |
TCP |
MQP |
This is the default port as defined in the server configuration. |
Detection server, WebApp server |
MS Server-sage (Local Threat Intel service) |
10443 |
HTTPS |
REST |
The connection used for air-gapped environments using the Local Threat Intel services of the Microservices Server for air-gapped deployment. |
Configuration management server |
MS Server |
15672 |
HTTP |
REST |
This is the default port as defined in the server configuration. |
Detection server |
MS Server (Arbiter microservice) |
8082 |
HTTP/2 |
gRPC (protobuf) |
This is the default port as defined in the server configuration. |
WebApp server |
MS Server (Management microservice) |
8088 |
HTTP/2 |
gRPC (protobuf) |
This is the default port as defined in the server configuration. |
WebApp server |
MS Server (BWL microservice) |
9021 |
HTTPS |
REST |
N/A |
Sensor (endpoint) |
Detection server |
8443/443 |
TCP |
RPC (protobuf) |
The port number is defined by the probe_port field in the Server_Configuration.csv file. |
Sensor (endpoint) |
Registration server |
8443/443 |
TCP |
RPC (protobuf) |
The port number is defined by the probe_port field in the Server_Configuration.csv file. |
MS Server (Arbiter) |
Detection server |
9073 |
HTTP/2 |
gRPC (protobuf) |
This port is used to synchronize the sensor policies configuration. |
WebApp server |
Local Threat Intel server |
443 |
HTTPS |
REST |
The connection used for air gapped environments using the Local Threat Intel server. |
Microservices - Local Threat Intel (Sage) |
Microservices Threat Intel database (MongoDB) |
27017 |
TCP |
N/A |
The connection is used for air-gapped environments using Microservices in air-gapped mode. |
Client PC |
NGAV Local update server (LUS) |
18443 |
HTTPS |
REST |
This connection is used to verify the status of the Local update server. |
Sensors |
Local update server (LUS) |
18443 |
HTTPS |
REST |
This port is used to fetch Malware updates from the Local update server. |
NGAV Local update server (LUS) |
Global update servers |
443 |
HTTPS |
REST |
This port is used by the NGAV Local update server to fetch updates from the Global update servers. This task can also be performed via a proxy, using external port 443. Relevant for AV Signature Protection only. |
All Cybereason Servers |
Configuration management server |
8500 |
HTTP |
REST |
This port is used for configuration tasks. |
Client PC |
Configuration management server |
8444 |
HTTPS |
N/A |
This port is used for the connection to the Zabbix UI. Do not use ports 443 or 8443. The Configuration management server uses these ports. |
Detection server |
WebApp server |
10443 |
HTTPS |
REST |
This port is used for adding detection servers to the environment |
Detection server, WebApp server |
MS Server-sage |
7070 |
HTTPS |
REST |
Required for threat intelligence |
Detection server, WebApp server |
MS Server (MDS) |
9090 |
HTTPS |
REST |
Required for threat intelligence |
Configuration management server |
All Cybereason servers |
10050 |
TCP |
N/A |
Zabbix Monitoring Connection |
All Cybereason servers |
Configuration management server |
10051 |
TCP |
N/A |
Zabbix Monitoring Connection |
MS Server (MDS) |
Detection Server |
8443 |
HTTPS |
REST |
Managing BAL and Malop Decisions |
Configuration management server |
LDAPS server |
636 |
TCP |
N/A |
SSO Configuration |
Client PC |
Configuration management server (Keycloak UI) |
10443 |
TCP |
N/A |
Keycloak UI for configuration of SSO settings |
Communication with Threat Intel services
Cybereason On-Prem environments use threat intelligence data in one of the following ways:
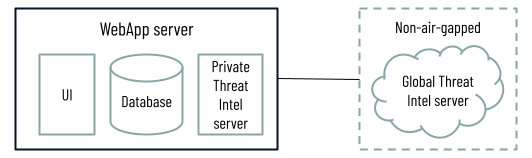
Cybereason environments connect to the cloud-hosted Global Threat Intel server, which leverages information from global intel sources to help determine the reputation of a given file, IP address, or domain. The connection is done using one of two options. For these environments, you can choose to connect to the Global Threat Intel server directly or to connect using a proxy.
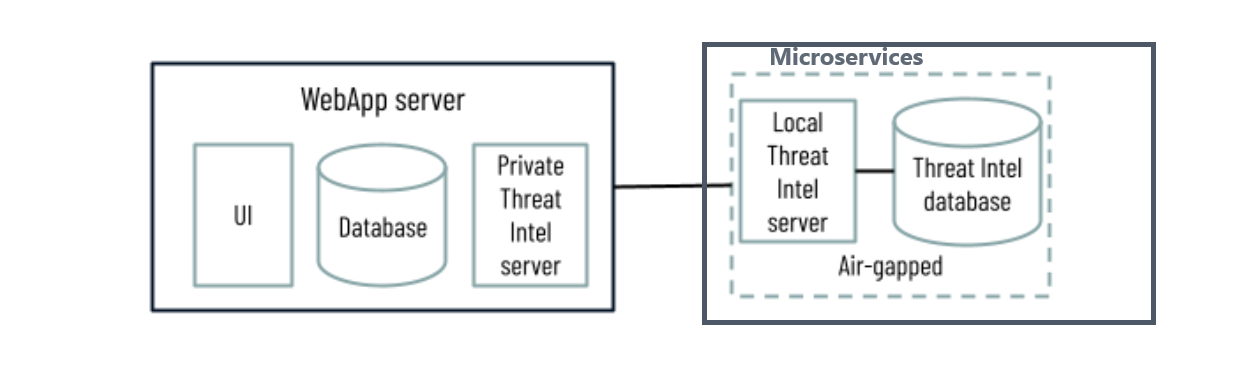
Cybereason On-Prem (on-premises) environments that cannot connect to the Global Threat Intel server use a containerized Local Threat Intel service, which allows you to add reputation records or to request Cybereason to pre-populate the server.
Option 1: Environments with a Global Threat Intel server
Communication between threat intel components
Source |
Ports |
Destination |
Comments |
|---|---|---|---|
WebApp server |
443 |
Global Threat Intel server (sage.cybereason.com) |
The connection used for external communication for non-air gapped deployments, see option 1 in the Communication with Threat Intel services section. This connection applies both to direct and proxy connections. |
Option 2: Environments with Local Threat Intel server and threat intel database
Communication between threat intel components
Source |
Ports |
Destination |
Comments |
|---|---|---|---|
WebApp server |
10443 |
Local Threat Intel sage container (part of the Microservices server) |
The connection used for air-gapped environments using the Local Threat Intel server, see option 2 in the Communication with Threat Intel services section. This connection applies both to direct and proxy connections. |
Local Threat Intel (Sage) server (part of the Microservices server) |
27017 |
Local Threat Intel database container (part of the Microservices server) |
The connection is used for air-gapped environments using the Local Threat Intel server, see option 2 in the Communication with Threat Intel services section. This connection applies both to direct and proxy connections. |
Communication certificates
The Cybereason servers communicate to each other and to the sensors using TLS. To establish TLS communication, certificates are required. Certificates that are used for this communication on the servers are stored in /opt/puppet-cybereason/ssl/.
Certificate diagram
Communication certificates include the following:
server.jks
client.jks
sage.jks
server_certificate.jks / global.jks
Certificate configuration files
There are three configuration files:
Server properties: /opt/puppet-cybereason/configuration.d/server-setup.properties
Server.xml: /opt/apache-tomcat-8.5.93/conf/server.xml
Global Threat Intel properties: /opt/puppet-cybereason/configuration.d/sage-setup.properties
Configuration issues in these files and parameters will cause the application to fail in:
Starting
Binding ports
The following tables describe the certificates that are used by each server type and their relative configuration files.
Detection server certificates
Usage |
Certificate |
Configuration File |
Parameters |
Description |
|---|---|---|---|---|
Internal Communication |
Server.jks |
|
Server properties:
Server.xml:
|
Registration <==> Detection Server WebApp Server <==> Detection Server |
Sensor communication |
server_certificate.jks / global.jks |
Server Properties |
|
Sensor <==> Detection Server |
WebApp server/Private Threat Intel server/Cybereason UI certificates
Usage |
Certificate |
Configuration File |
Parameters |
Description |
|---|---|---|---|---|
Presentation |
Server.jks |
Server.xml |
|
User <==> UI (browser) |
Internal communication |
client.jks |
Server Properties |
|
Detection Server <==> WebApp Server Registration Server<==> WebApp Server |
Private Threat Intel communication |
sage.jks |
Sage Properties |
|
Detection Server <==> Private Threat Intel Server |
Registration server certificates
Usage |
Certificate |
Configuration File |
Parameters |
Description |
|---|---|---|---|---|
Internal Communication |
client.jks |
Server properties |
|
Detection Server <==> Registration Server |
Internal Communication |
server.jks |
Server.xml |
|
WebApp Server <==> Registration Server |
Sensor communication |
server_certificate.jks / global.jks |
Server Properties |
|
Sensor <==> Registration Server |
Configuration management server certificate
Usage |
Certificate |
Configuration File |
Parameters |
Description |
|---|---|---|---|---|
Presentation (web UI access) |
<name>.cert |
webui.service |
N/A |
Client Web Browser <==> Configuration Management Server |
Built-in server certificate for POC deployments
For POCs only, Cybereason On-Prem installations currently include a built-in server certificate created by Cybereason. The certificate’s CN is *.cr-poc.com. The server’s default configuration is designed to work with this certificate. The Cybereason certificate is intended for very specific use cases, and requires that you configure the hosts file or the DNS server to resolve according to the configured FQDN.